Commits on Source (165)
Showing
- .ci/generator 1 addition, 1 deletion.ci/generator
- .gitlab-ci.yml 1 addition, 1 deletion.gitlab-ci.yml
- cards.md 35 additions, 21 deletionscards.md
- external/contribute/ssh-key-generation/ssh-key-generation.md 1 addition, 1 deletionexternal/contribute/ssh-key-generation/ssh-key-generation.md
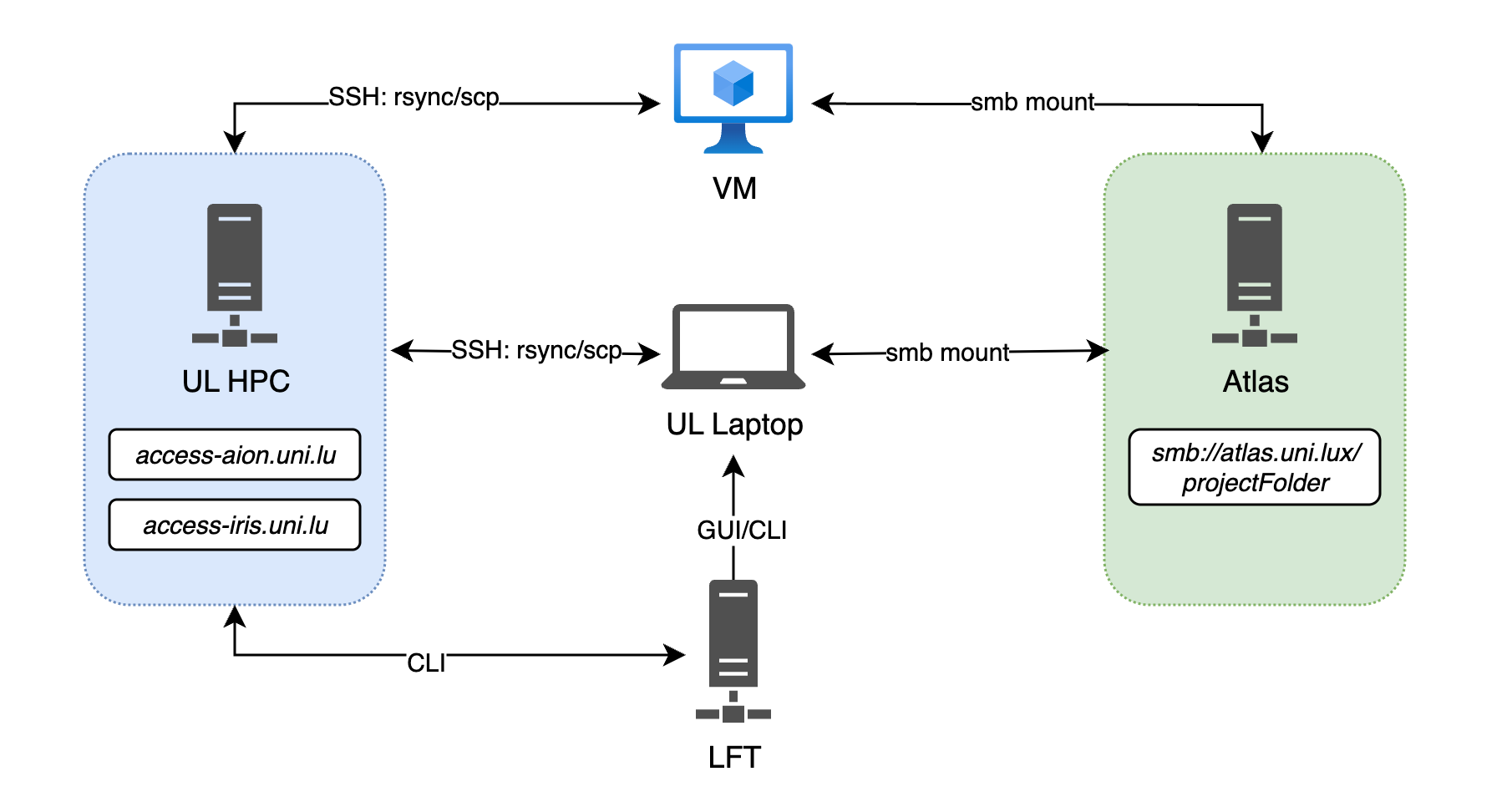
- external/exchange-channels/atlas-hpc/atlas-hpc.md 46 additions, 0 deletionsexternal/exchange-channels/atlas-hpc/atlas-hpc.md
- external/exchange-channels/atlas-hpc/img/data-transfer-flow.png 0 additions, 0 deletions...al/exchange-channels/atlas-hpc/img/data-transfer-flow.png
- external/exchange-channels/cryptomator/cryptomator.md 21 additions, 18 deletionsexternal/exchange-channels/cryptomator/cryptomator.md
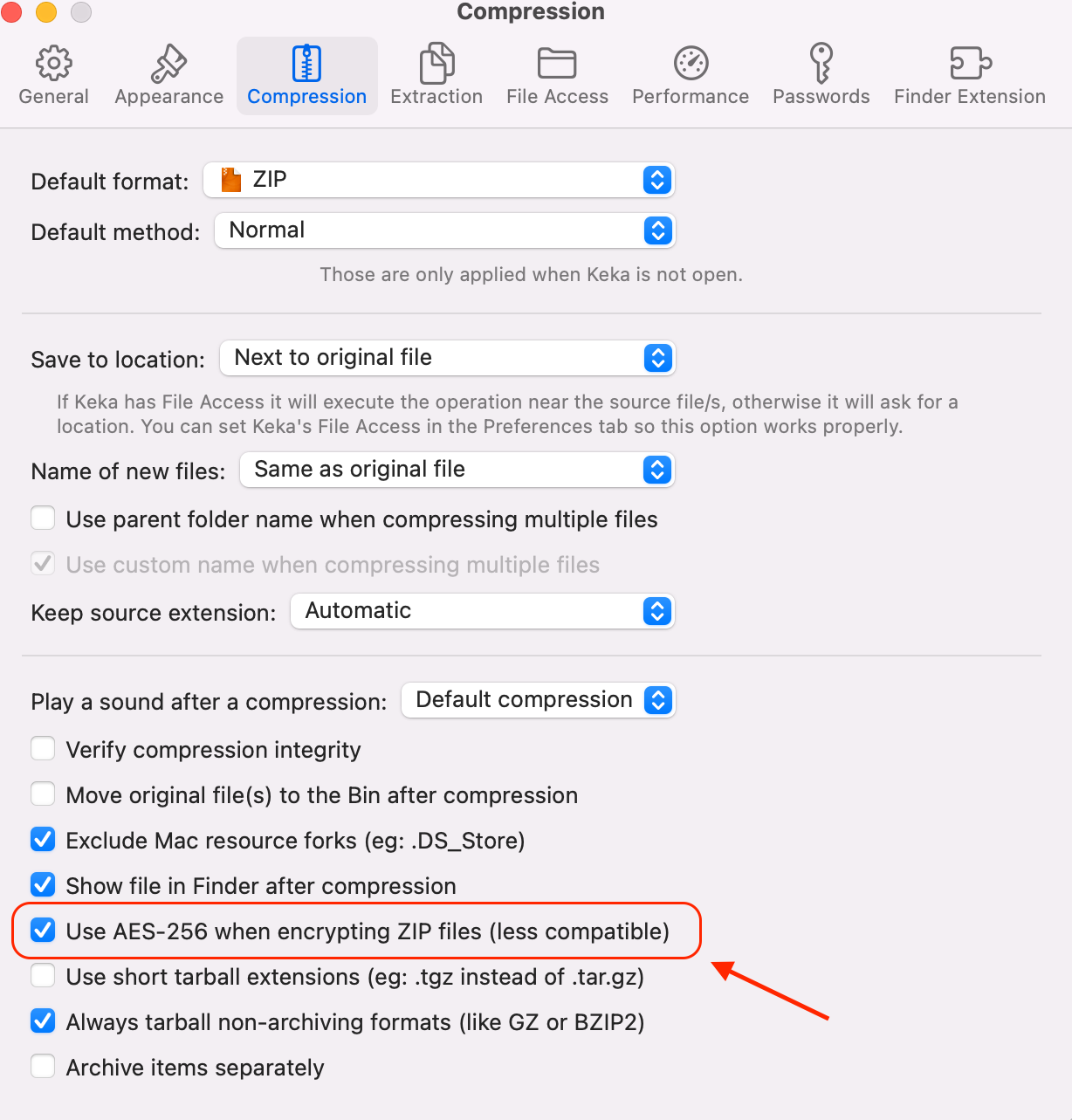
- external/integrity/encryption/file/encryption_file.md 6 additions, 11 deletionsexternal/integrity/encryption/file/encryption_file.md
- external/integrity/transfer/owncloud-privatebin/img/7zpassword.png 0 additions, 0 deletions...integrity/transfer/owncloud-privatebin/img/7zpassword.png
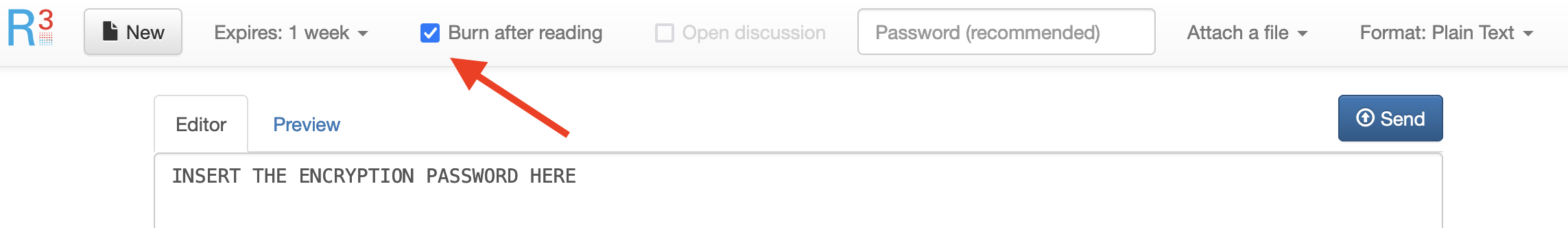
- external/integrity/transfer/owncloud-privatebin/img/encryptionpassword.png 0 additions, 0 deletions...y/transfer/owncloud-privatebin/img/encryptionpassword.png
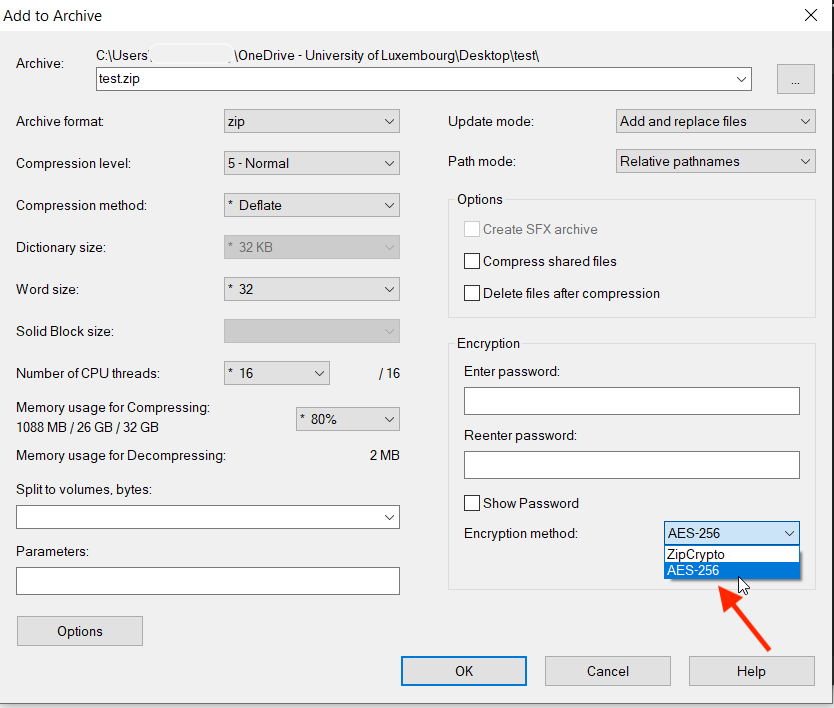
- external/integrity/transfer/owncloud-privatebin/img/keka-encryption.png 0 additions, 0 deletions...rity/transfer/owncloud-privatebin/img/keka-encryption.png
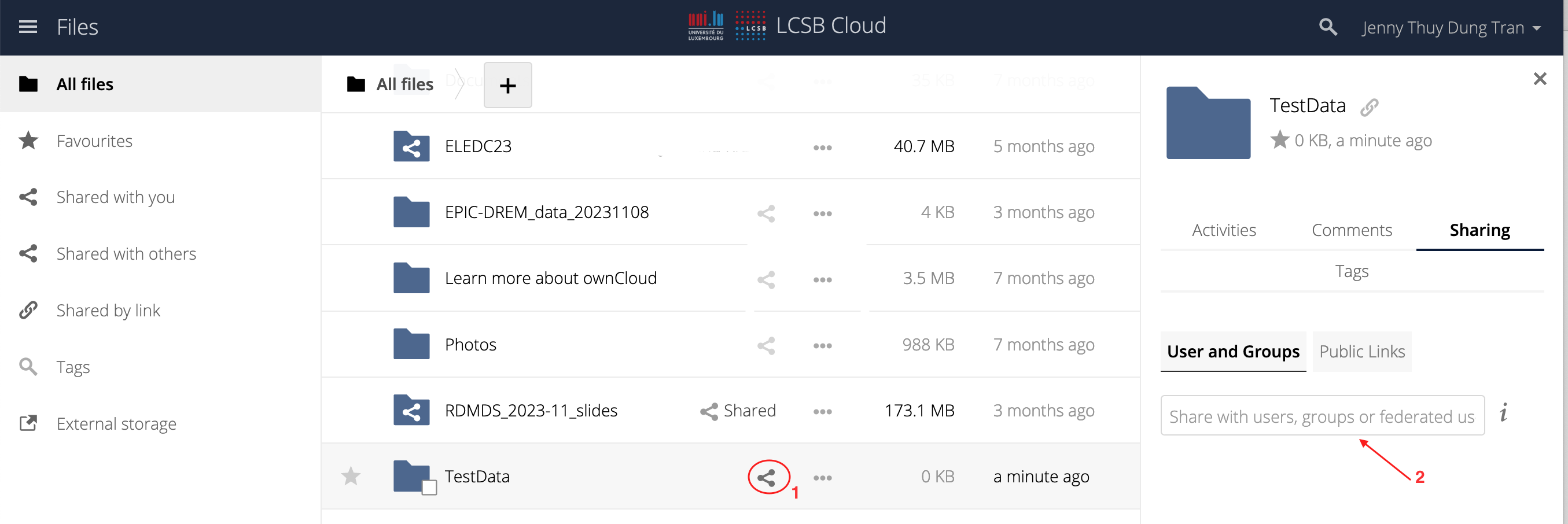
- external/integrity/transfer/owncloud-privatebin/img/owncloudshare.png 0 additions, 0 deletions...egrity/transfer/owncloud-privatebin/img/owncloudshare.png
- external/integrity/transfer/owncloud-privatebin/img/passwordLink.png 0 additions, 0 deletions...tegrity/transfer/owncloud-privatebin/img/passwordLink.png
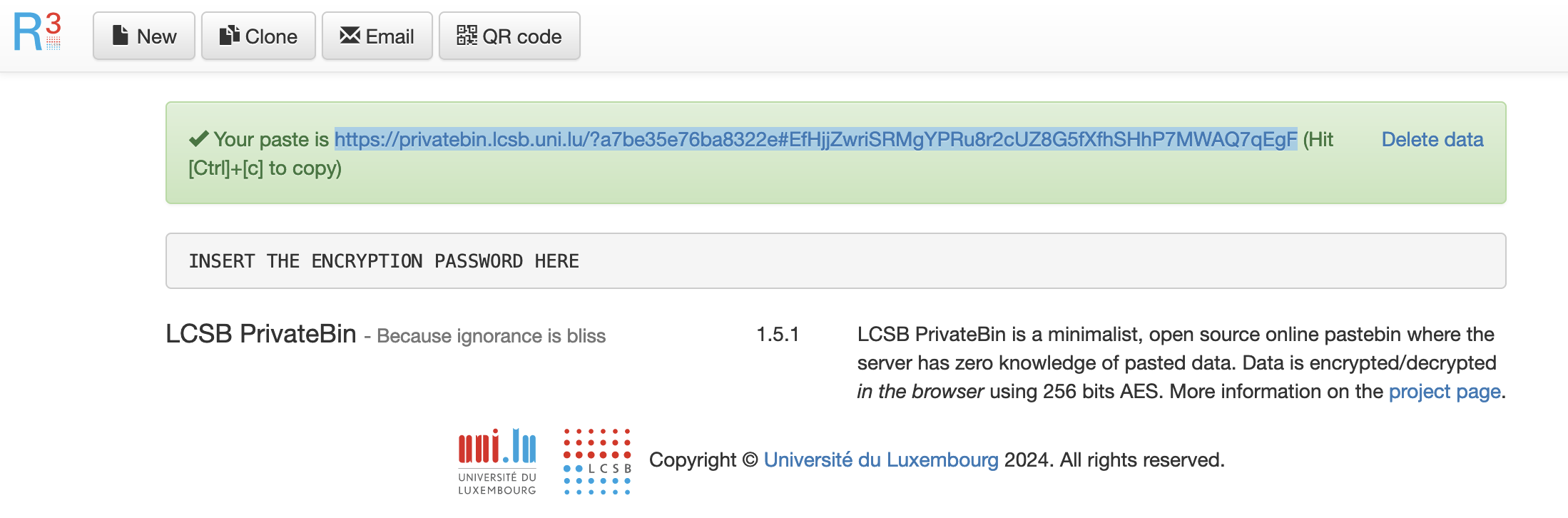
- external/integrity/transfer/owncloud-privatebin/owncloud-privatebin.md 38 additions, 0 deletions...grity/transfer/owncloud-privatebin/owncloud-privatebin.md
- external/lab-equipment/autoclaves/autoclaves.md 10 additions, 3 deletionsexternal/lab-equipment/autoclaves/autoclaves.md
- external/lab-equipment/autoclaves/img/img1.png 0 additions, 0 deletionsexternal/lab-equipment/autoclaves/img/img1.png
- external/lab-equipment/autoclaves/img/img10.png 0 additions, 0 deletionsexternal/lab-equipment/autoclaves/img/img10.png
- external/lab-equipment/autoclaves/img/img11.png 0 additions, 0 deletionsexternal/lab-equipment/autoclaves/img/img11.png
- external/lab-equipment/autoclaves/img/img12.png 0 additions, 0 deletionsexternal/lab-equipment/autoclaves/img/img12.png
- external/lab-equipment/autoclaves/img/img13.png 0 additions, 0 deletionsexternal/lab-equipment/autoclaves/img/img13.png
127 KiB
60.2 KiB
67.9 KiB
248 KiB
223 KiB
197 KiB
File moved
File moved
File moved
File moved
File moved